ERC4626
ERC4626 is an extension of ERC20 that proposes a standard interface for token vaults. This standard interface can be used by widely different contracts (including lending markets, aggregators, and intrinsically interest bearing tokens), which brings a number of subtleties. Navigating these potential issues is essential to implementing a compliant and composable token vault.
We provide a base component of ERC4626 which is designed to allow developers to easily re-configure the vault’s behavior, using traits and hooks, while staying compliant. In this guide, we will discuss some security considerations that affect ERC4626. We will also discuss common customizations of the vault.
Security concern: Inflation attack
Visualizing the vault
In exchange for the assets deposited into an ERC4626 vault, a user receives shares. These shares can later be burned to redeem the corresponding underlying assets. The number of shares a user gets depends on the amount of assets they put in and on the exchange rate of the vault. This exchange rate is defined by the current liquidity held by the vault.
-
If a vault has 100 tokens to back 200 shares, then each share is worth 0.5 assets.
-
If a vault has 200 tokens to back 100 shares, then each share is worth 2.0 assets.
In other words, the exchange rate can be defined as the slope of the line that passes through the origin and the current number of assets and shares in the vault. Deposits and withdrawals move the vault in this line.
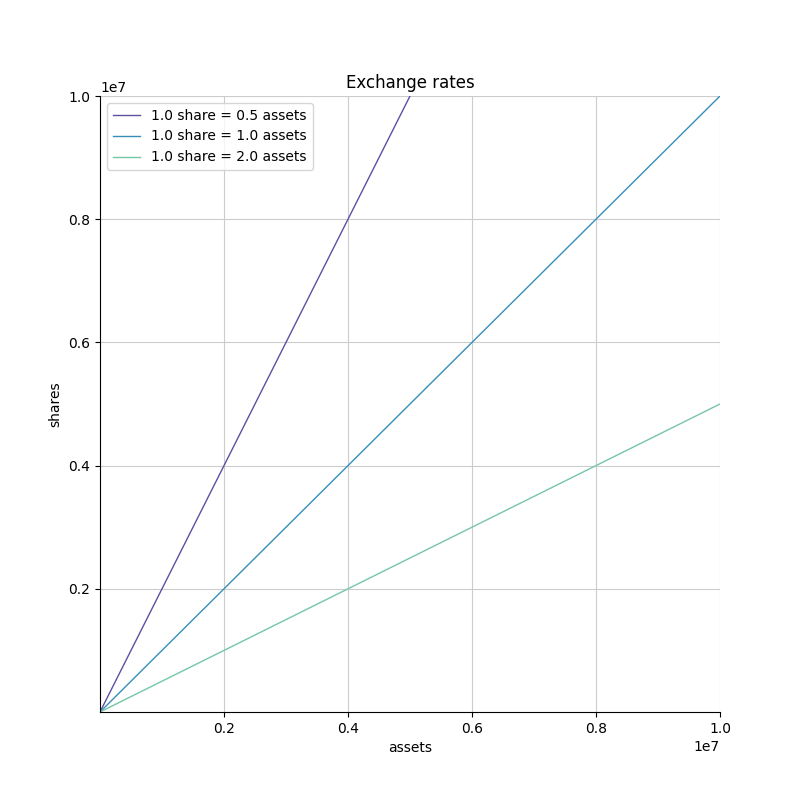
When plotted in log-log scale, the rate is defined similarly, but appears differently (because the point (0,0) is infinitely far away). Rates are represented by "diagonal" lines with different offsets.
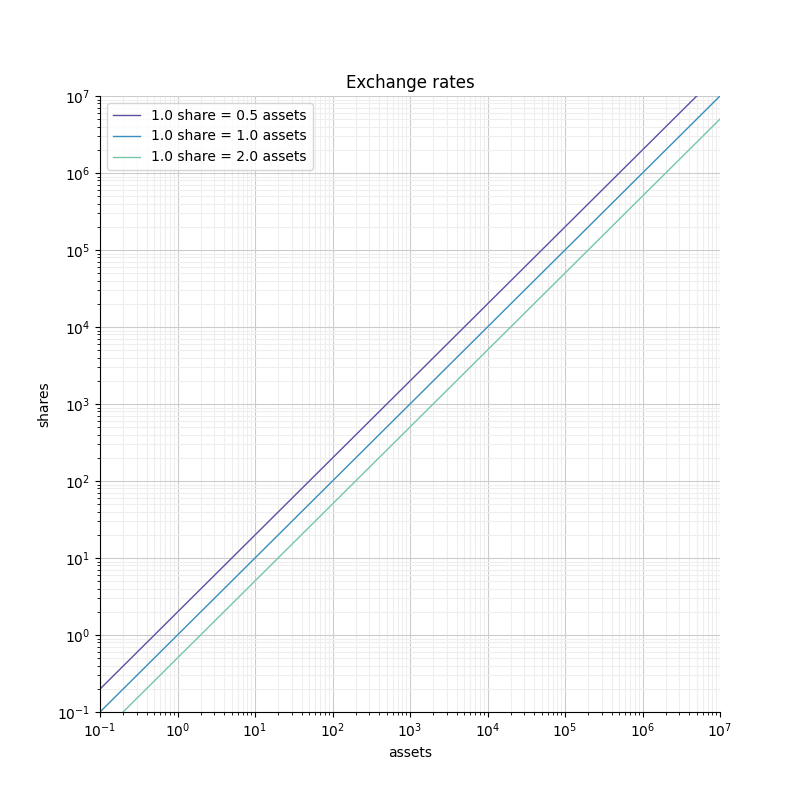
In such a representation, widely different rates can be clearly visible in the same graph. This wouldn’t be the case in linear scale.
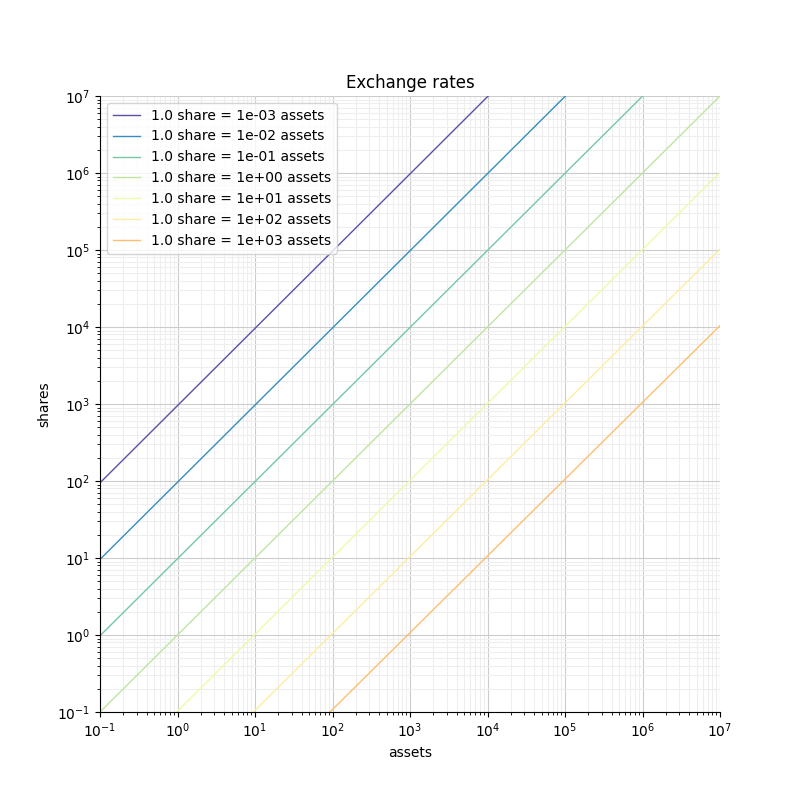
The attack
When depositing tokens, the number of shares a user gets is rounded towards zero. This rounding takes away value from the user in favor of the vault (i.e. in favor of all the current shareholders). This rounding is often negligible because of the amount at stake. If you deposit 1e9 shares worth of tokens, the rounding will have you lose at most 0.0000001% of your deposit. However if you deposit 10 shares worth of tokens, you could lose 10% of your deposit. Even worse, if you deposit less than 1 share worth of tokens, you will receive 0 shares, effectively making a donation.
For a given amount of assets, the more shares you receive the safer you are. If you want to limit your losses to at most 1%, you need to receive at least 100 shares.
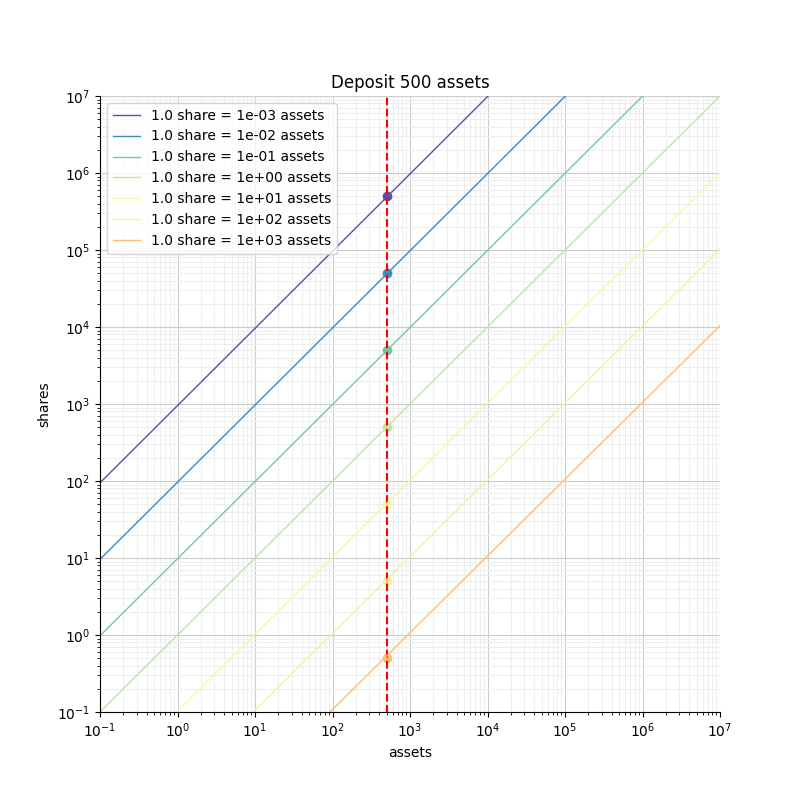
In the figure we can see that for a given deposit of 500 assets, the number of shares we get and the corresponding rounding losses depend on the exchange rate. If the exchange rate is that of the orange curve, we are getting less than a share, so we lose 100% of our deposit. However, if the exchange rate is that of the green curve, we get 5000 shares, which limits our rounding losses to at most 0.02%.
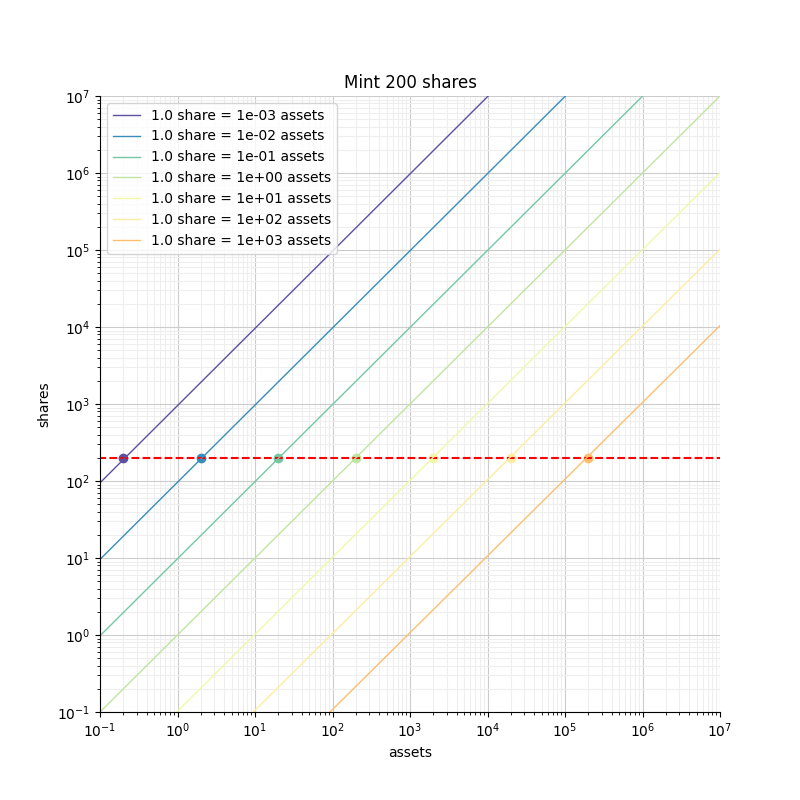
Symmetrically, if we focus on limiting our losses to a maximum of 0.5%, we need to get at least 200 shares. With the green exchange rate that requires just 20 tokens, but with the orange rate that requires 200000 tokens.
We can clearly see that the blue and green curves correspond to vaults that are safer than the yellow and orange curves.
The idea of an inflation attack is that an attacker can donate assets to the vault to move the rate curve to the right, and make the vault unsafe.
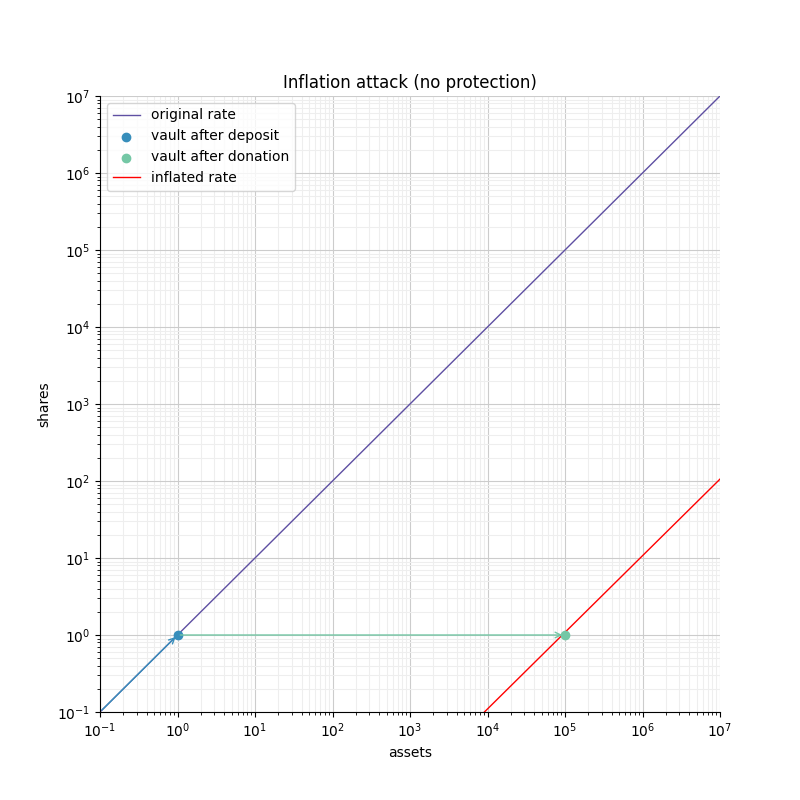
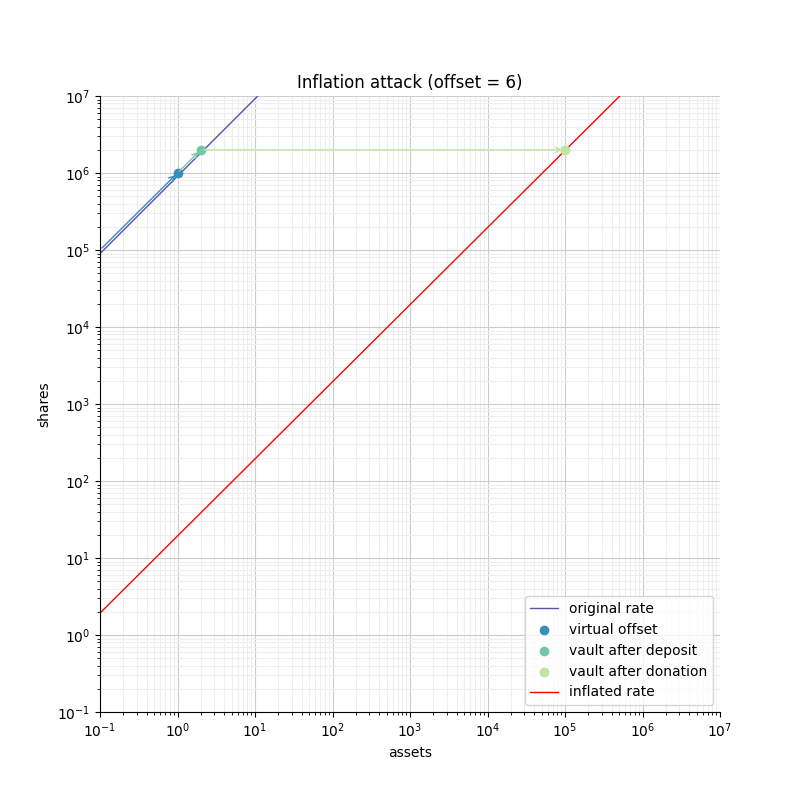
Figure 6 shows how an attacker can manipulate the rate of an empty vault. First the attacker must deposit a small amount of tokens (1 token) and follow up with a donation of 1e5 tokens directly to the vault to move the exchange rate "right". This puts the vault in a state where any deposit smaller than 1e5 would be completely lost to the vault. Given that the attacker is the only shareholder (from their donation), the attacker would steal all the tokens deposited.
An attacker would typically wait for a user to do the first deposit into the vault, and would frontrun that operation with the attack described above. The risk is low, and the size of the "donation" required to manipulate the vault is equivalent to the size of the deposit that is being attacked.
In math that gives:
-
-
-
| Assets | Shares | Rate | |
|---|---|---|---|
initial |
- |
||
after attacker’s deposit |
|||
after attacker’s donation |
This means a deposit of
For the attacker to dilute that deposit to 0 shares, causing the user to lose all its deposit, it must ensure that
Using
It is easy to generalize the above results to scenarios where the attacker is going after a smaller fraction of the user’s deposit. In order to target
In this scenario, the attack is
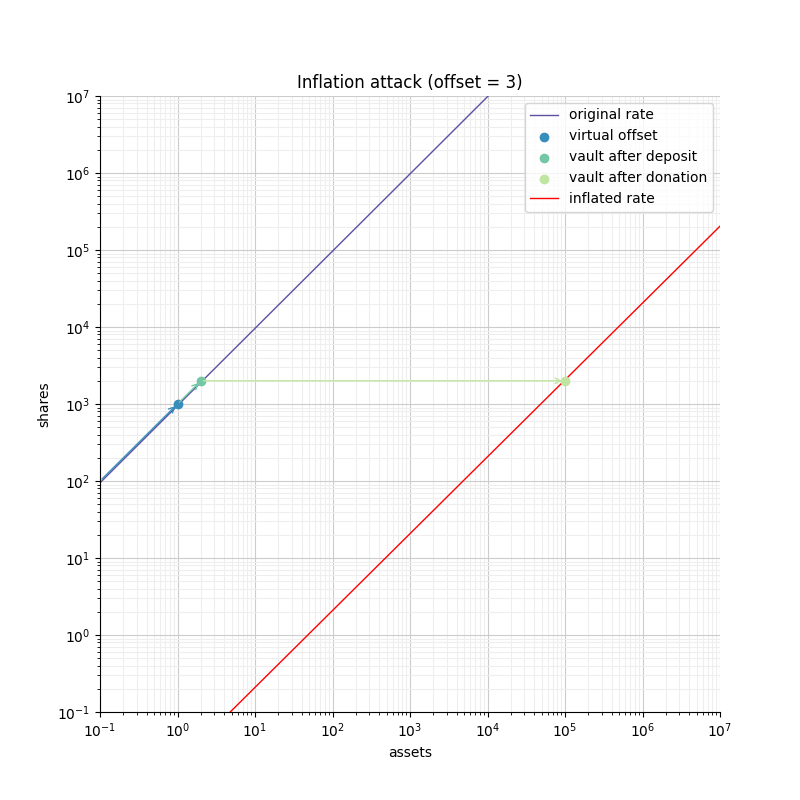
Defending with a virtual offset
The defense we propose is based on the approach used in YieldBox. It consists of two parts:
-
Use an offset between the "precision" of the representation of shares and assets. Said otherwise, we use more decimal places to represent the shares than the underlying token does to represent the assets.
-
Include virtual shares and virtual assets in the exchange rate computation. These virtual assets enforce the conversion rate when the vault is empty.
These two parts work together in enforcing the security of the vault. First, the increased precision corresponds to a high rate, which we saw is safer as it reduces the rounding error when computing the amount of shares. Second, the virtual assets and shares (in addition to simplifying a lot of the computations) capture part of the donation, making it unprofitable to perform an attack.
Following the previous math definitions, we have:
-
-
-
-
| Assets | Shares | Rate | |
|---|---|---|---|
initial |
|||
after attacker’s deposit |
|||
after attacker’s donation |
One important thing to note is that the attacker only owns a fraction
When the user deposits
For the attacker to dilute that deposit to 0 shares, causing the user to lose all its deposit, it must ensure that
-
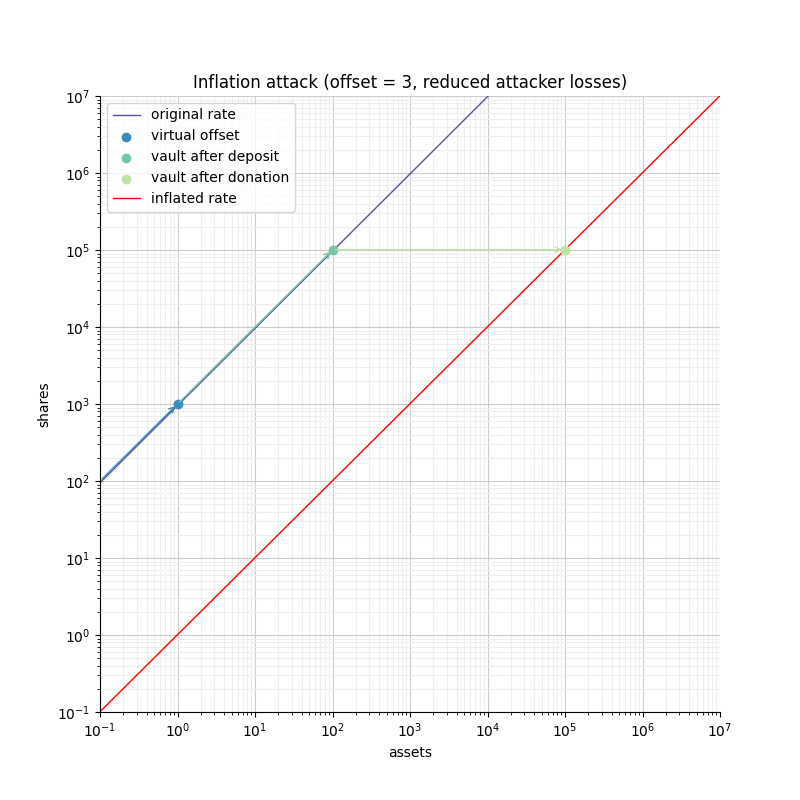
If the offset is 0, the attacker loss is at least equal to the user’s deposit.
-
If the offset is greater than 0, the attacker will have to suffer losses that are orders of magnitude bigger than the amount of value that can hypothetically be stolen from the user.
This shows that even with an offset of 0, the virtual shares and assets make this attack non profitable for the attacker. Bigger offsets increase the security even further by making any attack on the user extremely wasteful.
The following figure shows how the offset impacts the initial rate and limits the ability of an attacker with limited funds to inflate it effectively.
Usage
Custom behavior: Adding fees to the vault
In ERC4626 vaults, fees can be captured during the deposit/mint and/or during the withdraw/redeem steps. In both cases, it is essential to remain compliant with the ERC4626 requirements in regard to the preview functions.
For example, if calling deposit(100, receiver), the caller should deposit exactly 100 underlying tokens, including fees, and the receiver should receive a number of shares that matches the value returned by preview_deposit(100).
Similarly, preview_mint should account for the fees that the user will have to pay on top of share’s cost.
As for the Deposit event, while this is less clear in the EIP spec itself,
there seems to be consensus that it should include the number of assets paid for by the user, including the fees.
On the other hand, when withdrawing assets, the number given by the user should correspond to what the user receives.
Any fees should be added to the quote (in shares) performed by preview_withdraw.
The Withdraw event should include the number of shares the user burns (including fees) and the number of assets the user actually receives (after fees are deducted).
The consequence of this design is that both the Deposit and Withdraw events will describe two exchange rates.
The spread between the "Buy-in" and the "Exit" prices correspond to the fees taken by the vault.
The following example describes how fees proportional to the deposited/withdrawn amount can be implemented:
/// The mock contract charges fees in terms of assets, not shares.
/// This means that the fees are calculated based on the amount of assets that are being deposited
/// or withdrawn, and not based on the amount of shares that are being minted or redeemed.
/// This is an opinionated design decision for the purpose of testing.
/// DO NOT USE IN PRODUCTION
#[starknet::contract]
pub mod ERC4626Fees {
use openzeppelin_token::erc20::extensions::erc4626::ERC4626Component;
use openzeppelin_token::erc20::extensions::erc4626::ERC4626Component::FeeConfigTrait;
use openzeppelin_token::erc20::extensions::erc4626::ERC4626Component::InternalTrait as ERC4626InternalTrait;
use openzeppelin_token::erc20::extensions::erc4626::{DefaultConfig, ERC4626DefaultLimits};
use openzeppelin_token::erc20::interface::{IERC20Dispatcher, IERC20DispatcherTrait};
use openzeppelin_token::erc20::{ERC20Component, ERC20HooksEmptyImpl};
use openzeppelin_utils::math;
use openzeppelin_utils::math::Rounding;
use starknet::ContractAddress;
use starknet::storage::{StoragePointerReadAccess, StoragePointerWriteAccess};
component!(path: ERC4626Component, storage: erc4626, event: ERC4626Event);
component!(path: ERC20Component, storage: erc20, event: ERC20Event);
// ERC4626
#[abi(embed_v0)]
impl ERC4626ComponentImpl = ERC4626Component::ERC4626Impl<ContractState>;
// ERC4626MetadataImpl is a custom impl of IERC20Metadata
#[abi(embed_v0)]
impl ERC4626MetadataImpl = ERC4626Component::ERC4626MetadataImpl<ContractState>;
// ERC20
#[abi(embed_v0)]
impl ERC20Impl = ERC20Component::ERC20Impl<ContractState>;
#[abi(embed_v0)]
impl ERC20CamelOnlyImpl = ERC20Component::ERC20CamelOnlyImpl<ContractState>;
impl ERC4626InternalImpl = ERC4626Component::InternalImpl<ContractState>;
impl ERC20InternalImpl = ERC20Component::InternalImpl<ContractState>;
#[storage]
pub struct Storage {
#[substorage(v0)]
pub erc4626: ERC4626Component::Storage,
#[substorage(v0)]
pub erc20: ERC20Component::Storage,
pub entry_fee_basis_point_value: u256,
pub entry_fee_recipient: ContractAddress,
pub exit_fee_basis_point_value: u256,
pub exit_fee_recipient: ContractAddress,
}
#[event]
#[derive(Drop, starknet::Event)]
enum Event {
#[flat]
ERC4626Event: ERC4626Component::Event,
#[flat]
ERC20Event: ERC20Component::Event,
}
const _BASIS_POINT_SCALE: u256 = 10_000;
/// Hooks
impl ERC4626HooksEmptyImpl of ERC4626Component::ERC4626HooksTrait<ContractState> {
fn after_deposit(
ref self: ERC4626Component::ComponentState<ContractState>, assets: u256, shares: u256,
) {
let mut contract_state = self.get_contract_mut();
let entry_basis_points = contract_state.entry_fee_basis_point_value.read();
let fee = contract_state.fee_on_total(assets, entry_basis_points);
let recipient = contract_state.entry_fee_recipient.read();
if fee > 0 && recipient != starknet::get_contract_address() {
contract_state.transfer_fees(recipient, fee);
}
}
fn before_withdraw(
ref self: ERC4626Component::ComponentState<ContractState>, assets: u256, shares: u256,
) {
let mut contract_state = self.get_contract_mut();
let exit_basis_points = contract_state.exit_fee_basis_point_value.read();
let fee = contract_state.fee_on_raw(assets, exit_basis_points);
let recipient = contract_state.exit_fee_recipient.read();
if fee > 0 && recipient != starknet::get_contract_address() {
contract_state.transfer_fees(recipient, fee);
}
}
}
/// Adjust fees
impl AdjustFeesImpl of FeeConfigTrait<ContractState> {
fn adjust_deposit(
self: @ERC4626Component::ComponentState<ContractState>, assets: u256,
) -> u256 {
let contract_state = self.get_contract();
contract_state.remove_fee_from_deposit(assets)
}
fn adjust_mint(
self: @ERC4626Component::ComponentState<ContractState>, assets: u256,
) -> u256 {
let contract_state = self.get_contract();
contract_state.add_fee_to_mint(assets)
}
fn adjust_withdraw(
self: @ERC4626Component::ComponentState<ContractState>, assets: u256,
) -> u256 {
let contract_state = self.get_contract();
contract_state.add_fee_to_withdraw(assets)
}
fn adjust_redeem(
self: @ERC4626Component::ComponentState<ContractState>, assets: u256,
) -> u256 {
let contract_state = self.get_contract();
contract_state.remove_fee_from_redeem(assets)
}
}
#[constructor]
fn constructor(
ref self: ContractState,
name: ByteArray,
symbol: ByteArray,
underlying_asset: ContractAddress,
initial_supply: u256,
recipient: ContractAddress,
entry_fee: u256,
entry_treasury: ContractAddress,
exit_fee: u256,
exit_treasury: ContractAddress,
) {
self.erc20.initializer(name, symbol);
self.erc20.mint(recipient, initial_supply);
self.erc4626.initializer(underlying_asset);
self.entry_fee_basis_point_value.write(entry_fee);
self.entry_fee_recipient.write(entry_treasury);
self.exit_fee_basis_point_value.write(exit_fee);
self.exit_fee_recipient.write(exit_treasury);
}
#[generate_trait]
pub impl InternalImpl of InternalTrait {
fn transfer_fees(ref self: ContractState, recipient: ContractAddress, fee: u256) {
let asset_address = self.asset();
let asset_dispatcher = IERC20Dispatcher { contract_address: asset_address };
assert(asset_dispatcher.transfer(recipient, fee), 'Fee transfer failed');
}
fn remove_fee_from_deposit(self: @ContractState, assets: u256) -> u256 {
let fee = self.fee_on_total(assets, self.entry_fee_basis_point_value.read());
assets - fee
}
fn add_fee_to_mint(self: @ContractState, assets: u256) -> u256 {
assets + self.fee_on_raw(assets, self.entry_fee_basis_point_value.read())
}
fn add_fee_to_withdraw(self: @ContractState, assets: u256) -> u256 {
let fee = self.fee_on_raw(assets, self.exit_fee_basis_point_value.read());
assets + fee
}
fn remove_fee_from_redeem(self: @ContractState, assets: u256) -> u256 {
assets - self.fee_on_total(assets, self.exit_fee_basis_point_value.read())
}
///
/// Fee operations
///
/// Calculates the fees that should be added to an amount `assets` that does not already
/// include fees.
/// Used in IERC4626::mint and IERC4626::withdraw operations.
fn fee_on_raw(self: @ContractState, assets: u256, fee_basis_points: u256) -> u256 {
math::u256_mul_div(assets, fee_basis_points, _BASIS_POINT_SCALE, Rounding::Ceil)
}
/// Calculates the fee part of an amount `assets` that already includes fees.
/// Used in IERC4626::deposit and IERC4626::redeem operations.
fn fee_on_total(self: @ContractState, assets: u256, fee_basis_points: u256) -> u256 {
math::u256_mul_div(
assets, fee_basis_points, fee_basis_points + _BASIS_POINT_SCALE, Rounding::Ceil,
)
}
}
}Interface
The following interface represents the full ABI of the Contracts for Cairo ERC4626Component. The full interface includes the IERC4626, IERC20, and IERC20Metadata interfaces. Note that implementing the IERC20Metadata interface is a requirement of IERC4626.
#[starknet::interface]
pub trait ERC4626ABI {
// IERC4626
fn asset() -> ContractAddress;
fn total_assets() -> u256;
fn convert_to_shares(assets: u256) -> u256;
fn convert_to_assets(shares: u256) -> u256;
fn max_deposit(receiver: ContractAddress) -> u256;
fn preview_deposit(assets: u256) -> u256;
fn deposit(assets: u256, receiver: ContractAddress) -> u256;
fn max_mint(receiver: ContractAddress) -> u256;
fn preview_mint(shares: u256) -> u256;
fn mint(shares: u256, receiver: ContractAddress) -> u256;
fn max_withdraw(owner: ContractAddress) -> u256;
fn preview_withdraw(assets: u256) -> u256;
fn withdraw(
assets: u256, receiver: ContractAddress, owner: ContractAddress,
) -> u256;
fn max_redeem(owner: ContractAddress) -> u256;
fn preview_redeem(shares: u256) -> u256;
fn redeem(
shares: u256, receiver: ContractAddress, owner: ContractAddress,
) -> u256;
// IERC20
fn total_supply() -> u256;
fn balance_of(account: ContractAddress) -> u256;
fn allowance(owner: ContractAddress, spender: ContractAddress) -> u256;
fn transfer(recipient: ContractAddress, amount: u256) -> bool;
fn transfer_from(
sender: ContractAddress, recipient: ContractAddress, amount: u256,
) -> bool;
fn approve(spender: ContractAddress, amount: u256) -> bool;
// IERC20Metadata
fn name() -> ByteArray;
fn symbol() -> ByteArray;
fn decimals() -> u8;
// IERC20CamelOnly
fn totalSupply() -> u256;
fn balanceOf(account: ContractAddress) -> u256;
fn transferFrom(
sender: ContractAddress, recipient: ContractAddress, amount: u256,
) -> bool;
}