Logging
Defender generates log trails of every potentially relevant event in the system. This includes manual actions, such as modifying an Autotask or Sentinel, as well as automated actions, such as sending a transaction or firing a notification. Logs can be optionally forwarded to Datadog or Splunk for aggregation.
This is a premium feature, if you are interested in it let us know by filling in this form.
Use cases
Use Defender Logging for tracking all changes and actions on your system, such as:
-
Track user actions on your team by monitoring sign ins and activity across the application
-
Detect potential attacks on your infrastructure from failed sign in attempts
-
Follow relayer activity to understand the transactions being sent from your accounts
-
Keep an audit trail of all changes to your Autotasks, Sentinels, and Relayers
Log Entries
Every log entry will be assigned to one of autotask, sentinel, relay, admin, or account, and tagged with a severity level ranging from trace to error. Log entries track both the subject and object of the action, and categorize the event in one of the following:
-
added -
archived -
created -
deleted -
exceeded -
executed -
invited -
invoked -
notification -
paused -
proposed -
replaced -
sent -
set -
triggered -
updated -
invalid sign in -
signed in -
signed out'
Log Forwarding
Generated logs can be forwarded to Datadog and Splunk, or any other service that supports API Key authentication. You can use this to aggregate all logs across your infrastructure in a single place.
Setup Log Forwarding Destination
To set up a log forwarding destination, open the User Menu at the top right corner of Defender or click here.
You can access the log destination configuration page by pressing the Add Forwarding Destination button.
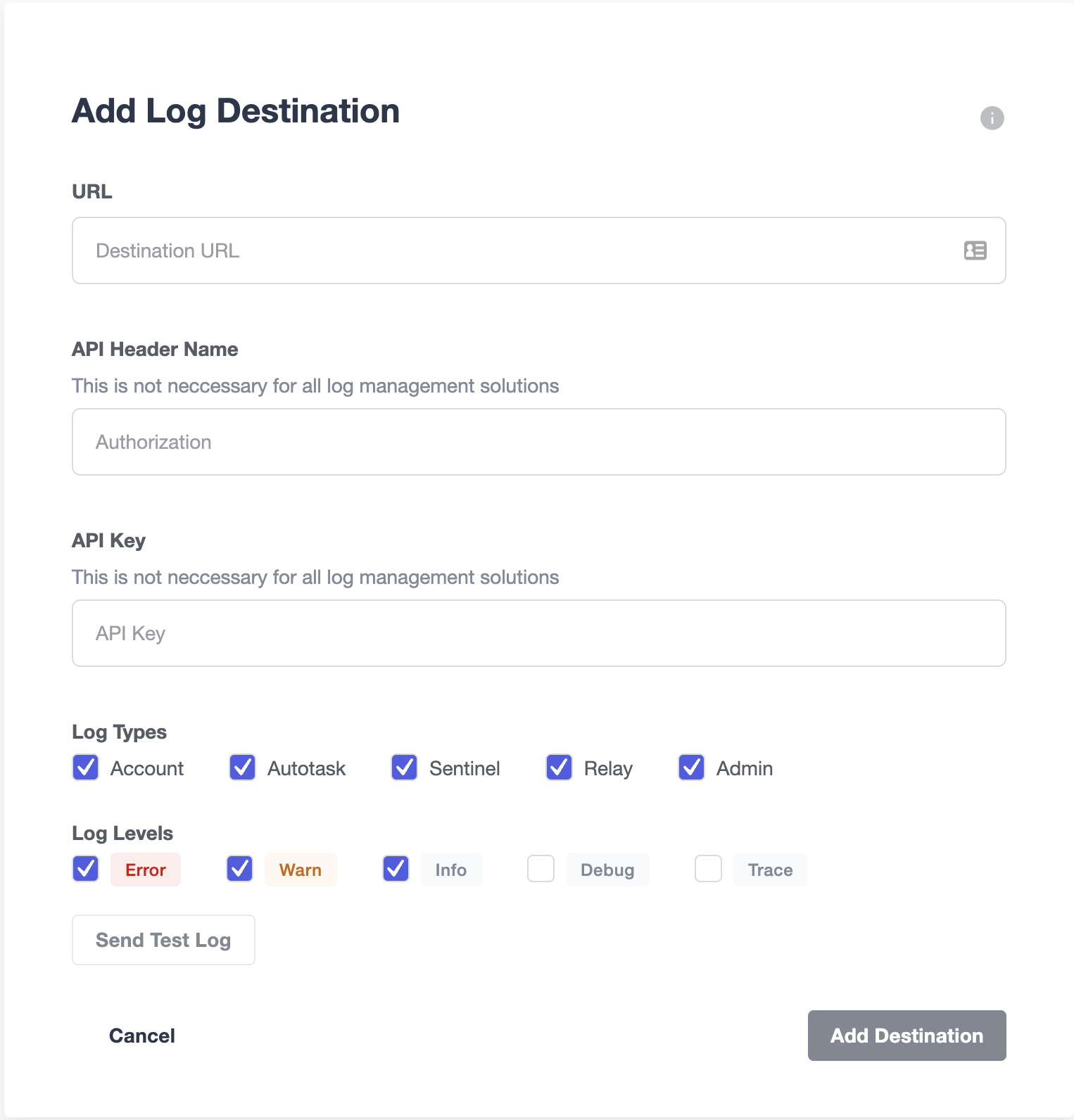
Form fields:
-
URL field is a required field. All logs are forwarded to this URL address using HTTP POSTs.
-
API Header Name is optional. This is the name of the request header that contains the API Key value. Most log management services require it. Please refer to your log management service documentation to determine if you need it.
-
API Key is an optional field. API Key is sent with every request for authentication purposes. Most log management services require it. Please refer to your log management service documentation to determine if you need it.
-
Log Types lets you specify which subset of Defender generated logs you want to have forwarded based on Defender components.
-
Log Levels lets you specify which subset of Defender generated logs you want to have forwarded based on the log levels. For example debug logs can be used for Autotasks debugging purposes and they can contain data that should not be exported to external systems.
| In the next section we will cover how to setup Log Forwarding with Splunk and Datadog but it is worth noting that Log Forwarding works with any other service that supports API Key authentication. |
Splunk
Forwarding logs to Splunk is done by using Splunk HEC(HTTP Event Collector). Documentation for setting up logging with Splunk HEC can be found here.
| Log Forwarding does not work with Splunk trial accounts because of Splunk internals. |
Example:
-
URL:
https://username.splunkcloud.com/services/collector/raw -
API Header Name:
Authorization -
API Key:
Splunk xxxxxxxxxxxxxxxxxxxxxxxxxxx
URL value is dynamic as URL includes account username.
|
API Key should contain Splunk prefix.
|
Datadog
Documentation for setting up logging on Datadog can be found here.
Example:
-
URL:
https://http-intake.logs.datadoghq.com/api/v2/logs -
API Header Name:
DD-API-KEY -
API Key:
xxxxxxxxxxxxxxxxxxxxxxxxxxx
Datadog uses different sites around the world. For example, if you are relying on an EU server the URL field value should be https://http-intake.logs.datadoghq.eu/api/v2/logs
|
API Key value can be obtained from Datadog site by opening Logs section from the left menu.
Go to Cloud section and select AWS provider.
After following those steps, the 'API Key` value is displayed in the bottom section of the page.
|